Modern VPN services often support multiple protocols, each designed with different priorities in mind. Some favour raw speed, others prioritise compatibility, and some are built for stability on mobile networks or restrictive environments.
Understanding how VPN protocols work — and when to use each one — can make a noticeable difference in performance, especially for streaming, gaming, travelling, or using VPNs on mobile devices.
In this guide, we break down the most commonly used VPN protocols, explain how they affect speed and security, and show which protocol is best suited for specific real-world use cases.
How VPN Protocols Affect Speed, Stability, and Security
VPN protocols define how data is encrypted, transported, and maintained between your device and a VPN server. While protocols are often marketed as “fast” or “secure,” their real-world performance depends on how they handle three core elements: encryption overhead, connection management, and network adaptability.
Understanding these mechanics helps explain why the same VPN can feel fast in one situation and sluggish in another — even before server distance or congestion comes into play.
Encryption Overhead
All VPN protocols encrypt data, but they do not do so in the same way. Encryption adds processing overhead, requiring your device and the VPN server to encrypt and decrypt every packet of data.
Modern protocols are designed to minimise this overhead by using efficient cryptographic methods and streamlined code paths. Older or more configurable protocols often trade raw speed for flexibility and compatibility.
Connection Management
VPN protocols also differ in how they establish and maintain connections. Some prioritise fast connection times and seamless reconnections, while others focus on reliability and verification at the cost of speed.
This is why certain protocols reconnect instantly when switching networks, while others require a full renegotiation that temporarily interrupts traffic.
Network Adaptability
Network conditions are rarely static. Wi-Fi interference, mobile handoffs, restrictive firewalls, and packet loss all affect VPN performance.
Protocols that adapt quickly to changing network conditions tend to feel faster and more stable, especially on mobile devices or public Wi-Fi. Protocols that prioritise strict verification may be slower but remain reliable in difficult environments.
Why Provider Implementation Matters
A VPN protocol does not operate in isolation. The way a VPN provider implements a protocol — including server hardware, routing logic, and privacy safeguards — often has a greater impact on performance than the protocol itself.
A well-implemented older protocol can outperform a poorly implemented modern one. This is why protocol choice should be considered alongside provider quality, infrastructure, and use case.
WireGuard: A Modern Protocol Built for Speed
WireGuard is a relatively modern VPN protocol designed to prioritise efficiency, simplicity, and performance. Unlike older protocols that evolved over many years, WireGuard was built with a clean-slate approach, focusing on reducing complexity while maintaining strong cryptographic standards.
Its design philosophy centres on doing fewer things, but doing them extremely well. This has made WireGuard popular among users who value fast connections, low latency, and stable performance across modern devices.
Why WireGuard Is Typically Faster
WireGuard achieves higher performance primarily through a streamlined codebase and efficient cryptographic primitives. By limiting configuration options and using modern encryption by default, it reduces processing overhead on both the client and server.
This efficiency often translates into quicker connection establishment, lower latency, and better throughput compared to more configurable protocols.
Connection Stability and Network Switching
One of WireGuard’s strengths is its ability to handle network changes gracefully. When switching between Wi-Fi and mobile networks, WireGuard typically resumes connections quickly without requiring a full renegotiation.
This makes it particularly suitable for laptops, smartphones, and other devices that frequently move between networks.
Security Model
WireGuard uses a fixed set of modern cryptographic algorithms rather than offering multiple configuration choices. This approach reduces the risk of weak or misconfigured encryption settings and simplifies auditing.
By design, WireGuard keeps minimal state information in memory while a connection is active. Reputable VPN providers typically combine this with additional privacy measures to ensure user activity is not logged or retained.
Limitations to Be Aware Of
Despite its advantages, WireGuard is not ideal for every situation.
- Firewall resistance: WireGuard traffic is easier to identify than protocols that can mimic standard HTTPS traffic.
- Provider dependence: Privacy protections rely heavily on how the VPN provider implements the protocol.
- Restricted networks: In highly censored or locked-down environments, WireGuard connections may be blocked more easily than older protocols.
When WireGuard Makes the Most Sense
WireGuard is generally a strong choice when speed and responsiveness matter most. It performs well for activities such as high-quality streaming, online gaming, and everyday browsing on modern devices.
However, in restrictive networks or scenarios where traffic disguise and maximum compatibility are required, other protocols may be more reliable.
OpenVPN: Proven Reliability and Maximum Compatibility
OpenVPN is one of the longest-standing VPN protocols still in widespread use. It has been actively developed and audited for over two decades, making it a common choice for users who prioritise reliability, configurability, and compatibility across restrictive networks.
While OpenVPN is generally slower than newer protocols, its flexibility allows it to function in environments where modern protocols struggle or fail.
Why OpenVPN Is Still Widely Used
OpenVPN’s strength lies in its adaptability. It can operate over both UDP and TCP, use a wide range of ports, and disguise VPN traffic as standard HTTPS traffic when necessary.
This capability makes OpenVPN particularly effective in restrictive networks, corporate environments, and regions where VPN traffic is actively blocked.
Security and Audit History
OpenVPN’s open-source codebase has been extensively reviewed by security researchers over many years. Its long audit history provides a level of trust that newer protocols have not yet accumulated.
This is one reason OpenVPN is often preferred by privacy-focused users and organisations handling sensitive data.
For a deeper look at how long-established protocols compare from a privacy perspective, see our Best No-Log VPNs analysis.
Performance Trade-offs
OpenVPN’s flexibility comes at a cost. Its larger codebase and negotiation process introduce additional overhead, which can result in slower speeds and longer reconnection times compared to more streamlined protocols.
When configured to prioritise speed, OpenVPN can still deliver solid performance, but it rarely matches the responsiveness of modern alternatives in latency-sensitive scenarios.
This performance difference is explained in more detail in our guide on why VPNs slow down internet connections.
When OpenVPN Makes Sense
- Using VPNs on restrictive or firewalled networks
- Bypassing censorship or deep packet inspection
- Prioritising proven security over raw speed
- Running VPN connections on older or legacy systems
Many VPN providers still rely on OpenVPN as a fallback protocol when modern options are unavailable or blocked. In practice, a well-implemented OpenVPN setup can outperform a poorly optimised modern protocol.
IKEv2: Stability and Reliability on Mobile Networks
IKEv2 (Internet Key Exchange version 2) is a VPN protocol commonly paired with IPSec and is widely used for its stability, especially on mobile devices. Unlike protocols that prioritise raw speed or configurability, IKEv2 focuses on maintaining a reliable connection as network conditions change.
This design makes IKEv2 particularly effective for smartphones, tablets, and laptops that frequently switch between Wi-Fi and cellular networks.
Why IKEv2 Performs Well on Mobile
One of IKEv2’s defining features is its ability to quickly re-establish VPN connections when a network changes. When a device moves between access points or transitions from Wi-Fi to mobile data, IKEv2 typically resumes the tunnel without noticeable interruption.
This behaviour reduces dropped connections, stalled downloads, and disrupted calls — issues that are common with protocols that require full renegotiation after network changes.
Native Operating System Support
Many operating systems include built-in support for IKEv2, allowing users to configure VPN connections without installing additional software. Native integration often results in improved stability and lower battery usage compared to third-party VPN applications.
This simplicity makes IKEv2 a practical option for users who want VPN protection without extensive configuration.
Security Characteristics
When implemented with IPSec, IKEv2 supports strong encryption standards and secure key exchange mechanisms. It is widely used in enterprise environments where consistent performance and predictable behaviour are required.
As with other protocols, real-world security depends on how the VPN provider implements logging policies and infrastructure safeguards. For broader context, see our overview of no-log VPN practices.
Performance Trade-offs
IKEv2 generally delivers solid speeds but is not designed to maximise throughput in the same way as modern lightweight protocols. In latency-sensitive tasks such as competitive gaming, other protocols may feel more responsive.
That said, its stability can result in better real-world performance for users on unstable or frequently changing networks.
When IKEv2 Is the Best Choice
- Mobile-first usage on smartphones and tablets
- Frequent travel with changing networks
- Users who value stability over peak speeds
- Situations where native OS support is preferred
For users who experience frequent VPN dropouts or inconsistent connections, IKEv2 can offer a smoother experience than protocols focused primarily on speed.
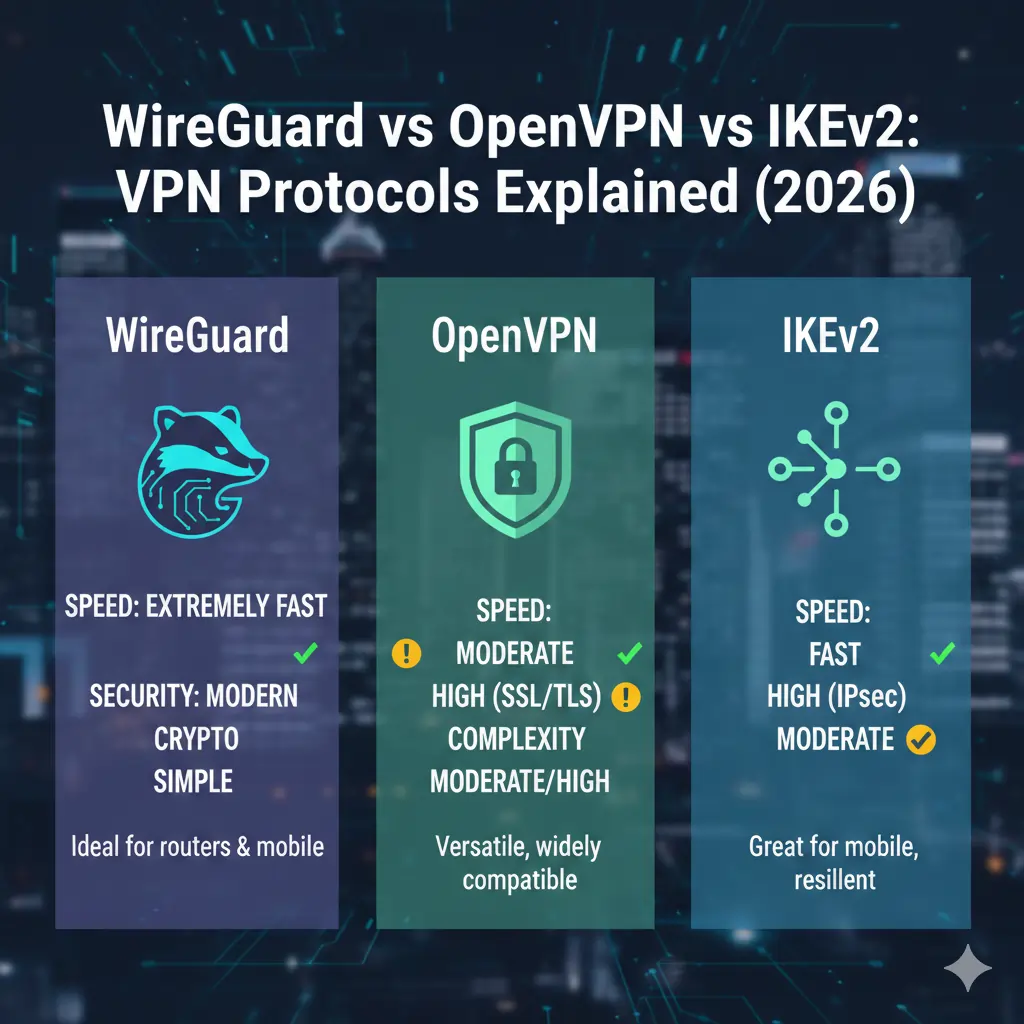
WireGuard vs OpenVPN vs IKEv2: Practical Comparison
Each VPN protocol is optimised for different priorities. Rather than ranking protocols as universally “best,” the table below highlights how they behave in real-world conditions and which scenarios they are best suited for.
| Protocol | Speed Characteristics | Stability | Security Approach | Best Use Cases |
|---|---|---|---|---|
| WireGuard | Low overhead, fast connection setup, low latency | Very stable on modern networks | Fixed modern cryptography, minimal configuration | Streaming, gaming, everyday browsing on modern devices |
| OpenVPN | Higher overhead, slower negotiation | Highly reliable across varied networks | Extensive configuration, long audit history | Restricted networks, privacy-focused use, enterprise setups |
| IKEv2 | Efficient on mobile, quick reconnections | Excellent during network changes | Strong encryption via IPSec implementations | Mobile devices, travel, frequent Wi-Fi/cellular switching |
Performance differences are influenced by device capability, network quality, and how a VPN provider implements each protocol. For context on how protocol choice affects overall performance, see our guide on why VPNs are slow.
Which VPN Protocol Should You Use?
The best VPN protocol depends on how and where you use a VPN. Rather than choosing a protocol based on marketing claims, it is more effective to match protocol behaviour to real-world scenarios.
For Streaming and Everyday Use
For most users streaming video, browsing the web, or using general online services, modern lightweight protocols provide the best balance of speed and reliability.
WireGuard-based protocols are commonly preferred in these situations due to their low overhead and fast connection handling. Real-world performance, however, depends heavily on how a VPN provider implements the protocol.
To see how popular implementations differ in practice, our NordLynx vs Lightway vs WireGuard speed analysis breaks down protocol behaviour beyond the underlying specification.
For Gaming and Latency-Sensitive Activities
Gaming performance is influenced by latency consistency more than peak download speeds. Protocols with fast reconnection and minimal processing overhead tend to feel more responsive during gameplay.
This is explored further in our guide to the best VPNs for gaming, where protocol choice is evaluated alongside server routing and stability.
For Privacy-Focused and Restricted Networks
In environments where VPN traffic is actively restricted or monitored, flexibility and traffic disguise matter more than raw speed.
OpenVPN remains one of the most reliable choices in these situations due to its ability to operate over common ports and blend into standard HTTPS traffic. This behaviour is discussed in more depth in our analysis of VPN performance trade-offs.
For Mobile Devices and Travel
Mobile users frequently experience network changes that can disrupt VPN connections. Protocols designed for fast reconnection often deliver better real-world performance on smartphones and tablets.
IKEv2 is commonly chosen for this reason, particularly when native operating system support and stability are priorities.
When Protocol Choice Matters Less
In many cases, the VPN provider’s infrastructure has a greater impact on performance than the protocol itself. Server quality, routing efficiency, and congestion management often outweigh protocol differences.
This is why protocol selection should be considered alongside provider reliability, as outlined in our Fastest VPNs comparison.
Final Thoughts: Why VPN Speed Is About Trade-Offs, Not Myths
VPN speed issues are rarely caused by a single factor. Protocol choice, server distance, congestion, encryption overhead, and device performance all interact to influence real-world results.
Modern protocols such as WireGuard, OpenVPN, and IKEv2 each prioritise different strengths. Faster performance often means lower overhead, while greater flexibility and obfuscation typically introduce speed trade-offs.
The most reliable way to improve VPN performance is not blindly switching protocols, but understanding how protocols behave in different scenarios and choosing providers that implement them correctly.
For users who want deeper protocol-level testing, provider comparisons, and verified performance data, the resources below expand on each topic without repeating generic advice.
Related VPN Guides, Reviews & Comparisons
| Topic | What It Covers | Link |
|---|---|---|
| VPN Speed & Performance | Independent testing of providers with a focus on real-world speed | Fastest VPNs (2026) |
| Protocol Fundamentals | Why VPNs slow connections and how protocol choice affects performance | Why VPNs Are Slow (And How to Fix It) |
| Protocol Deep-Dive | Implementation-level speed testing of modern VPN protocols | NordLynx vs Lightway vs WireGuard |
| Streaming Performance | Protocol and routing impact on Netflix and major streaming platforms | Best VPNs for Streaming |
| Gaming Performance | Latency, jitter, and stability testing for online gaming | Best VPNs for Gaming |
| Privacy & Logging | How protocol choice interacts with no-log policies and audits | Best No-Log VPNs |
| VPN Trust & Risk | Providers with performance or privacy concerns to avoid | VPNs to Avoid |
Frequently Asked Questions
Which VPN protocol is the fastest?
WireGuard is currently the fastest VPN protocol in real-world testing. Its lightweight design reduces encryption overhead, resulting in lower latency and higher sustained speeds compared to OpenVPN and IKEv2.
Is WireGuard secure enough for privacy?
Yes, when implemented correctly by reputable VPN providers. WireGuard uses modern cryptography, but privacy depends on how providers handle IP address management and session data.
Why is OpenVPN slower than WireGuard?
OpenVPN has a much larger codebase and greater configurability, which increases CPU overhead. This flexibility improves reliability and firewall traversal but comes at the cost of speed.
Which VPN protocol is best for mobile devices?
IKEv2/IPSec is generally the best option for mobile users because it handles network switching efficiently and is supported natively on most operating systems.
Can switching VPN protocols improve speed?
Yes. Switching from OpenVPN to WireGuard or IKEv2 often results in noticeable speed improvements, especially for streaming, gaming, and large downloads.
Should I use different protocols for different activities?
Absolutely. Many users prefer WireGuard for streaming and gaming, OpenVPN for privacy-sensitive tasks, and IKEv2 for mobile use.
Related VPN Guides, Reviews & Comparisons
The guides below expand on VPN protocols, speed optimisation, provider
performance, and real-world use cases. Each resource is based on
independent testing and detailed analysis.
| Category | Page | What You’ll Learn |
|---|---|---|
| VPN Speed | Fastest VPNs (2026) | Independent speed testing across protocols, regions, and real-world usage scenarios. |
| VPN Performance | Why VPNs Are Slow (And How to Fix It) | Technical causes of VPN slowdowns and practical optimisation methods. |
| Protocol Testing | NordLynx vs Lightway vs WireGuard | Real-world speed and latency comparison of modern VPN protocols. |
| VPN Reviews | NordVPN Review | In-depth testing of NordLynx, OpenVPN performance, and privacy controls. |
| VPN Reviews | Surfshark Review | WireGuard speed, streaming reliability, and mobile performance analysis. |
| VPN Reviews | IPVanish Review | Protocol stability, mobile speed, and IKEv2 implementation testing. |
| VPN Reviews | ExpressVPN Review | Lightway protocol performance and OpenVPN reliability in restricted networks. |
| Gaming | Best VPNs for Gaming | Low-latency VPN testing for competitive and casual online gaming. |
| Streaming | Best VPNs for Streaming | Protocol impact on Netflix, Disney+, Prime Video, and buffering. |
| Privacy | Best No-Log VPNs | How protocol choice interacts with audits, logging, and jurisdiction. |
| Trust | VPNs to Avoid | Providers with poor protocol implementation or privacy risks. |